The programs that are not recognized usually find their way to the systems of the technical users without any warning, and the software Keepho5ll is one of the most baffling ones. It often leaves scripts in project directories, system directories, or downloads, causing confusion to the developers, IT professionals, and advanced users. Since it has the ability of running background processes and interpret configuration files, as well as execute hidden processes, most users find it difficult to judge whether it is an internal tool or a potential threat. The guide provides information on how software Keepho5ll operates, its loading code, and the risks that it can present, and the procedure of inspecting or handling it safely.
Who Should Use Software Keepho5ll?
Software Keepho5ll keeps a technical script from being executed and its own start-up processes that are not required in legacy or customized projects. It is not a consumer application, and the average user will have no reason to use it. Its primary job is to run loading code that initiates particular tasks when a system or application starts, and so, for maintenance technicians and developers, it’s important.
This software is primarily used by:
- The company’s IT crowd checks systems and unknown files and has a look at the software behavior.
- Developers who trust keepho5ll scripts with their old code, internal applications, or projects whose work has been put on ice.
- Technical professionals and researchers who examine the behavior of software or unknown files.
If you are not a user of those groups, as a rule, you shouldn’t install Keepho5ll. If you’re unaware of how the loading code works, opening it up could result in things like system errors occurring, unrecognized scripts running, etc. The more you know about who applies it, the better you can judge whether it’s relevant to your own work and if you should be taking risks in using it.
Key Features of Software Keepho5ll
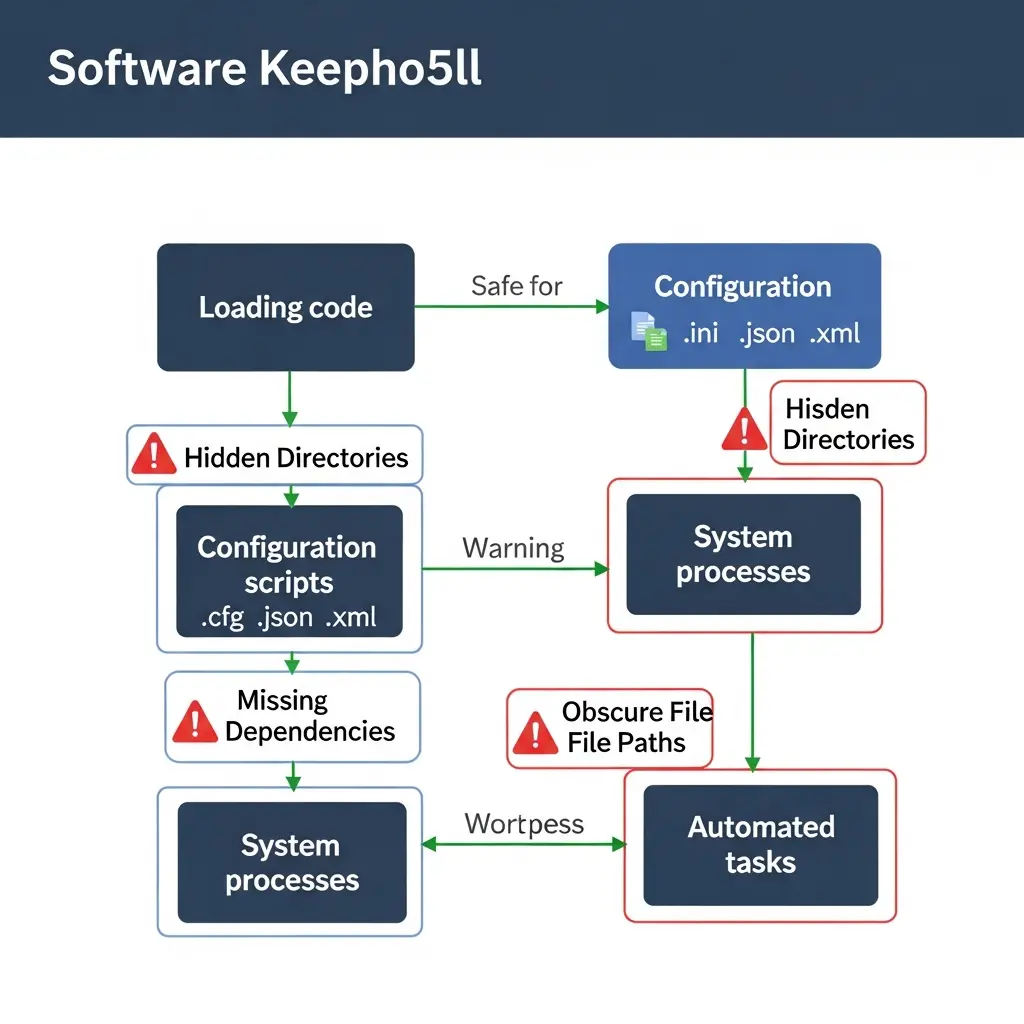
Software Keepho5ll is not merely a file in your system but a tool that executes software scripts, controls startup processes, and also communicates with system files. The knowledge of its features can guide technical users to work with it safely and effectively.
What the software keepho5ll loading code does
- Launches background scripts on the program’s start.
- Read or update configuration files (.cfg, .ini, .json, .xml) to set up dependencies.
- Interact with system processes or other apps where necessary for internal tools.
- Runs automated tasks, like booting services or inspecting directories.
Why Users Face Problems
- Hidden scripts are hidden because their hosting directory is a typically obscure place.
- Users may attempt to directly run obfuscated files, but they are incomprehensible.
- If you have missing or old dependencies, it can lead to errors (or catastrophic failure!) in the system.
Actionable Steps to Inspect Safely
- Find the file of the loading code in the installation or project directory.
- Do not execute it directly yet, just to stop hidden processes from working.
- Open it with a text editor to view instructions, external references, and system commands.
- Verify the file type: .cfg, .ini, .xml, or .json are usually configuration scripts.
- Examine the entity creation or last modified date and file origin.
- Use your own antivirus/security software to scan the file for threats.
Configuration and System Interaction
Software Keepho5ll doesn’t just run scripts—it interfaces with system files and settings to make older or internal tools actually work. Knowledge of this interaction can assist technical users in troubleshooting errors and preventing system conflicts.
How Keepho5ll Uses Configuration Files
- Read configuration files (.cfg, .ini, .json, .xml) are used to configure necessary parameters.
- Automatically updates files and/or type code when system or application requirements change.
- Validates the dependencies before starting it.
- Looks up environment variables to determine if scripts run in the proper context.
System-Level Interactions
- Fires up background processes that some other application may rely on.
- Alters temp or log files during run.
- Interacts with directories and services to support existing workflows.
- It keeps track of the system state so as to ensure complete and updated components.
Common User Challenges
- Users have difficulty finding configuration files because they are located in hidden folders.
- When a script is unable to reach the necessary directories or services, it breaks.
- Weird behavior can be expected if the dependencies are not there or are outdated.
Documentation and Internal Notes
Software Keepho5ll looks to in-app documentation to take users by the hand. These files document dependencies and the process of configuration, as well as how to make the loading code work. The fact that notes are missing or old also confuses the users and can cause errors to occur.
Actionable Tips:
- Look for readings or notes in the software.
- Compare the instructions to the loading code before executing any scripts.
- If one does not exist, document it yourself.
- Write scripts to test in a sandbox and not on your main system.
Doing this makes it easy for you to understand who is Keepho5ll as well as not to commit errors while dealing with unknown scripts.
How Software Keepho5ll Works

Software Keepho5ll has a deliberate execution strategy that relies on its loader code, configuration files, and system-level access. The function goes into action as soon as the system or application activates it, without any user intervention needed.
There is code that automatically runs software Keepho5ll, and there is such a thing as booting it. This code validates that necessary directories exist, checks to ensure file paths are valid, and tests to see if dependent scripts are available. If the code cannot find a specific file it needs, the program may halt with no error message or run in decremented mode instead.
Action: aware of it when you’re editing the loading code, and make sure to check file paths before running.
Then, Keepho5ll software reads the configuration files to determine how it should act. These files specify environment variables, startup policies, and execution constraints. Misconfigured or outdated settings are a common cause of background activity you didn’t expect.
Action: Review .cfg, .ini, .json, or. xml files and make sure the values are correct for your system layout.
Software Keepho5ll exchanges with the operating system after configuration verification. It could start background subprocesses, check the state of the system, or give directions to internal scripts. These operations proceed quietly, which is why many users see Keepho5ll when system behavior changes.
Action: Monitor the task manager and system logs to monitor running processes.
And lastly, the software Keepho5ll survives due to internal checks. The software can retry to execute if the dependencies are altered or files are lost, in which case it may work improperly.
Action: Log failing execution for troubleshooting and keep dependencies stable.
By knowing this process, the Software Keepho5ll users can govern this software, de-risk the code, and remain secure with their loading of code without any guesses.
Risks and Red Flags of Software Keepho5ll
Keepho5ll Software Description: The software can be a source of security threats or performance problems when users are unable to determine its origin. It only becomes evident when the system starts to lag or not respond as you expected.
Knowing risks allows users to detect the problems early on and abort execution, thus protecting their system.
Common Red Flags
Keepho5ll software is typically installed on the system and runs scripts without notification, one of the reasons why users get suspicious. Strange boot time behavior, poor system performance, or even unknown Windows whose origin isn’t actually known often indicates mis-configured programs that start up in the OS.
Action: Close the program, scan all files with an antivirus, and open in text editor the file that is loading software Keepho5ll and read what command executes.
Malware or Security Risks
Unconfirmed Keepho5ll Software can open up systems to vulnerabilities. How it works: Malware frequently appears to be an internally developed tool and employs a loading code, which is used to execute covert commands while remaining hidden.
Some users don’t know how to differentiate between legitimate scripts and malicious ones because they both look the same.
Response: Discourage Admin Access > Monitor network access. Check the app in a sandbox before full execution.
Technical Challenges Users Face
Keepho5ll is the sort of software that can cause problems even when safe. Perhaps files fail to open, the loading code clashes with others or the software isn’t compatible with newer operating systems.
Action: Examine configuration files, error logs, and support system to determine if the problem you are encountering is normal.
How to Safely Use or Inspect Software Keepho5ll
The software Keepho5ll should not be executed by the user without checking its safety. Since it also performs scripts and background processes, close examination assists in avoiding system damage, loss of data, or possible security threats. Using a systematic approach enables users to examine software Keepho5ll and its loading code without subjecting their system to any risk.
Pre-Execution Safety Checks
The users are advised to scan all related files with updated antivirus or security software before running software Keepho5ll. The step assists in identifying the known threats prior to the execution of any script. The file properties should also be inspected by the users in terms of version, developer names and timestamps.
Action: The software does not identify itself; then it should be treated like an untrusted program and should not be executed.
Analyzing Loading Code Without Risk
The software Keepho5ll loading code should be analyzed by a user using a text editor rather than being executed. With this technique, it is possible to inspect commands, file paths and system calls safely. Configuration reads and file checks are considered safe signs, whereas hidden downloads, registry edits, and external network calls are considered suspicious.
Action: cease when the code carries out something that is not in line with its work
Backup and Recovery Planning
Before testing software Keepho5ll, it is always advisable that users should create a system and data backup. Files or settings can be changed by an unknown script without any form of notification.
Action: Backups of restore points or external backups must be used in order to recover quickly should there be a problem with execution.
When to Seek Technical Support
In case users are not able to guess the purpose of such software Keepho5ll, they should seek assistance. IT helpdesks are able to verify the ownership of the software in internal systems. It is also possible to analyze loading code safely by developer forums and cybersecurity professionals.
Action: Seek advice prior to the permission and execution of scripts.
Troubleshooting Common Problems
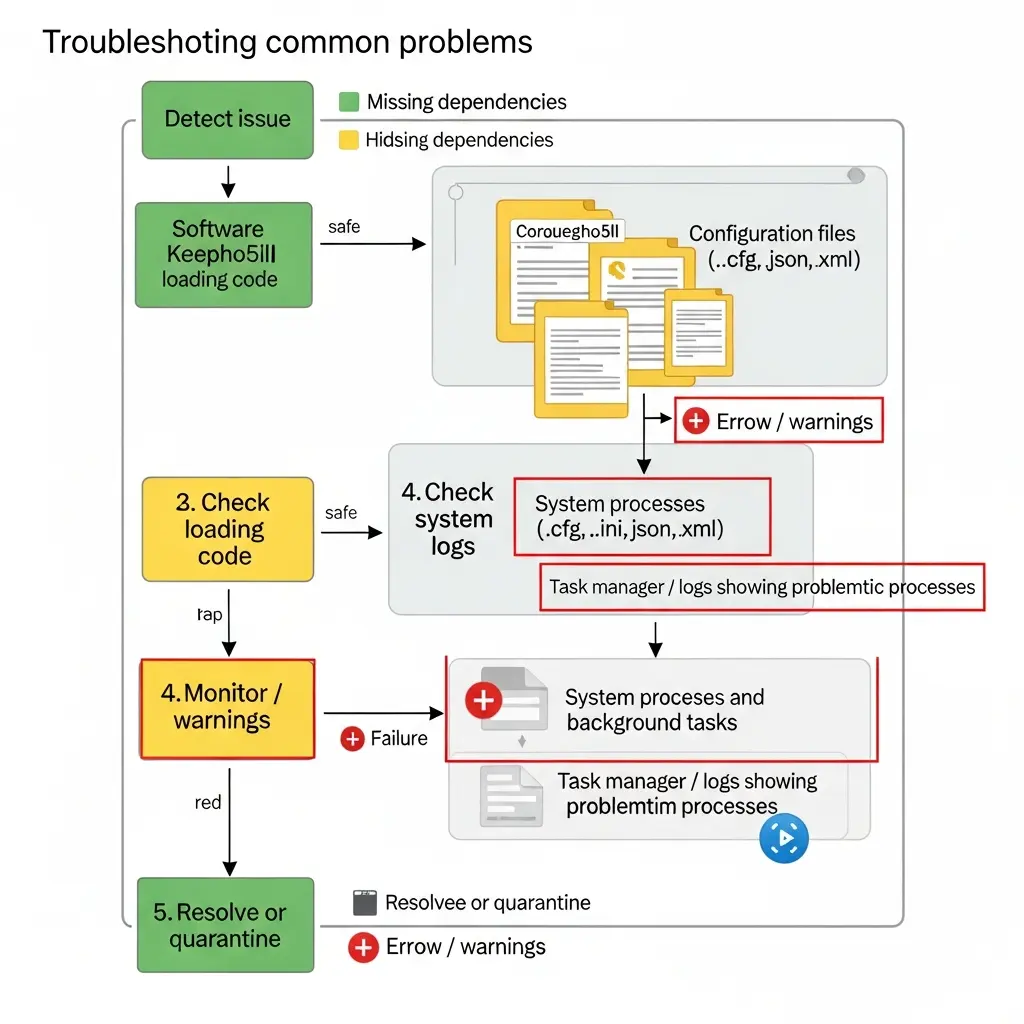
The software Keepho5ll is prone to causing problems in cases where it is executed on incompatible systems or where the configuration files are out of date. The majority of issues are associated with the startup failures, loading code errors, or unforeseen behavior of the system.
These steps will assist users in determining the root cause within a short time and rectifying the problem without endangering the stability of the system.
1. Software Won’t Launch
In the case that the software Keepho5ll does not start, it is mostly due to the absence of files or wrong permissions. The software can rely on configuration files or directories that have ceased to exist.
Action: Test file routes, ensure that there is read/write access, and finally test the presence of all the necessary files. The software is often found to have missing dependencies when running it in a controlled test environment.
2. Loading Code Errors or Warnings
Keepho5ll loading code software can cause errors with conflicting scripts and system settings, or a library out-of-date. The warnings are frequently displayed in case the code uses unsupported commands or unsuitable paths.
Action: Crack open the loading code in an editor, and read error messages and fix invalid references. The problem is normally solved by updating or isolating conflicting scripts.
3. Unexpected Behavior After Running Keepho5ll
Unforeseen behaviour is common where the software Keepho5ll is able to run background processes which are not visible to the user. Execution problems are indicated by system slowdown, excessive resource usage, or abnormal network activity.
Action: Terminate the software, check the processes running, and look at the system logs. In case of continuation of behavior, copy the files and reformat the system using a backup.
Unexpected Presence of Software Keepho5ll on Your Device
In some cases, software Keepho5ll can be found by the user when conducting a system audit, searching files, or troubleshooting a system. This is normally the case where old projects or shared workspaces, or bundled development files bring in tools that are not clearly interacted with by the user.
Users need not be threatened by this discovery, but take it as a diagnostic task that needs immediate response. A systematic review is used to decide on the validity of the technical purpose of the software or a hazard.
How to Analyze, Test, and Handle Software Keepho5ll Safely
Once the software Keepho5ll is found in the system of the user, one needs to look into it before executing or deleting it. Begin with the verification of the directory, file timestamps, and the project folders to identify the reason why the software is there. Projects that were old or environments used to test have internal tools left behind.
The second step is to open the software Keepho5ll loading code in a text editor and not execute it. Check scan files through security applications and check commands in order to determine safe actions and suspicious actions.
In case you cannot prove a valid reason to use the software, quarantine or isolate the software. Only delete it at a time when it has been confirmed that there are no system processes or projects that use it.
Conclusion:
Software Keepho5ll can enter your system in a particularly unforeseen way, and, even though it is capable of supporting internal tools and scripts, can generate errors or pose a security threat otherwise. To developers, IT professionals, and technical users, the trick is to look at the loading code, configurations and ensure to check the behavior of the system prior to execution.
It is essential to make sure that you back up your system, and in case the purpose of the software is not clear, quarantine or delete it to avoid any possible problems. These steps will make you sure that you can work with software Keepho5ll, make your system stable, and keep control over the unknown or outdated scripts.
FAQs
Q1: What is Software Keepho5ll?
Software Keepho5ll is a technical tool used by developers and IT professionals to run loading code and manage internal scripts. It’s not a consumer app and interacts with system files and configurations to support legacy or custom projects.
Q2: Who should use Software Keepho5ll?
Only technical users like developers, IT staff, and researchers should use it. If you’re unfamiliar with software Keepho5ll loading code, executing it can cause system errors or unexpected scripts.
Q3: Is Software Keepho5ll safe to use?
It is safe only if verified and from a trusted source. Always inspect its loading code, check configuration files (.cfg, .ini, .json, .xml), and scan files with antivirus software before execution.
Q4: What does software Keepho5ll loading code do?
The loading code initializes tasks, runs background scripts, reads configuration files, interacts with system processes, and can automate tasks. Misconfigured or hidden code may cause errors or system slowdowns.
Q5: How do I safely inspect Software Keepho5ll?
Open the loading code in a text editor without running it, verify file types, scan with security tools, and monitor system processes. Back up your system before testing unknown scripts.
Q6: What should I do if Software Keepho5ll appears unexpectedly on my system?
Check the directory, file timestamps, and project folders to determine its purpose. Inspect the loading code safely and, if uncertain, quarantine or remove the software. Monitor system logs if you decide to keep it.